The ongoing digital transformation of the recent decade has vastly changed our perception of excellent customer experience, with seamlessness becoming a (if not the) defining factor. The ease and comfort of making purchases and receiving services from virtually anywhere on the planet in one click however, comes at a price.
Seamless experiences largely depend on the use of consumers’ personal and sensitive data. Names, addresses, payment details — all of these help streamline the customer journey while simultaneously being a priceless bounty for cybercriminals. And should such data fall into criminals’ hands, you may consider your client lost forever.
77% of Australian, 75% of US and 88% of UK respondents say they would be unlikely to purchase from a company they didn’t trust.
Source: Okta
The tricky part about protecting the customer is that while they realise the value of their personal information and expect the brand to protect their data, they might not be equally ready to sacrifice their time and convenience in the name of their own security. As a result, brands have to maintain an equilibrium between protecting customers and making their CX as unobtrusive as possible.
What is wrong with user security anyways?
The short answer: the real problem lies with the users (and, ironically, their strive for seamlessness).
Passwords are the primary and most familiar means of protecting one’s account, and longer, complex passwords can serve as robust security measures of their own… given the user sticks to all security requirements and is always alert.
In reality, to make things simple and unobtrusive for themselves, people tend to reuse passwords across different sites. That is why users are advised to change all their passwords after any major data leak: the chances are that the leaked password might have been used elsewhere, and now all their logins are potentially vulnerable.
Even if one diligently comes up with a new password for each separate site or service, there is a great temptation to use a short and memorable word as a password — which makes it easy to crack via a brute-force or a dictionary attack: the former repeatedly tries guessing random combinations of characters until it finds a match, while the latter uses a list of commonly used words, checking them one-by-one.
At the same time, the more reliable, longer passwords that include numbers and symbols are harder to remember, which increases the risk of compromising post-its randomly occurring all over the user’s workplace, fridge or other places of habitat.
And then there is phishing — scams designed to collect one’s passwords. These can vary from simply calling the client as a bank’s customer service representative and asking for their password to “confirm their identity” to building a faux banking site login page to harvest the details. In either case, the criminal now has the user’s password and can access their account.
Multi-factor authentication
One of the most effective ways of protecting customers and their accounts is reinforcing the password with an additional means of identification on top of it.
Many enterprises, especially the ones involved with banking, crypto and e-commerce, use multi-factor authentication (MFA) to secure their customers’ information and accounts from account takeovers, identity theft or other fraudulent activities.
The way MFA works is when a user wants to access their account, they need to provide several authentication factors to prove their identity, hence the name. The most usual combination would be a username and a password combined with a second factor (and sometimes a third, fourth, and so on – what makes the difference between the two-factor authentication (2FA) and MFA). This other factor can involve something they have (like a phone or a security token) or something they are (like biometrics).
This way, compromised or simply weak passwords can be mitigated by also requiring a security code delivered over a device to which only the authorised user has access.
Mobile authentication
Device-based options (such as a phone or the aforementioned token) are unquestionably the most effective way of providing additional authentication factors. The problem with physical tokens is that they are really easy to lose, and even if one manages to keep them in sight, they still add unnecessary bulk to your keychain or pockets.
Most people have a mobile phone on them at all times, and we generally tend to keep a much better track of them and keep them locked more often, especially now with the rise of built-in biometrics. In fact, many mobile bank applications rely on biometrics to both secure access to an app and to make login more seamless. Even if a device is lost or stolen, getting into it will pose a challenge, so accessing a customer’s account will not be as easy.
Now that we have selected our optimal platform, it is time to pick a proper vehicle for authentication. Using third-party authentication apps like Google’s Authenticator might be a chore, and once again, they eat up additional space — this time in the device’s memory.
Sending push notifications in your own app might be a great seamless solution, given that the customer actually wants to download it. Another one would be to use a communications channel your client is already familiar and comfortable with — a messaging app they use daily, like Viber. This way, your client would also benefit from the built-in end-to-end encryption, which would give them even more peace of mind when it comes to their sensitive data.
But what if your client has to travel, lives in a remote area without proper access to mobile data, or simply prefers a feature phone over a more sophisticated device? You will require a ubiquitous channel that ensures rapid delivery and high open rates.
Delivering one-time passwords (OTPs) via A2P SMS is the best compromise between safety and security, as this allows Enterprises to protect their customers regardless of their location, without forcing them to use any additional software or hardware, swiftly delivering the OTPs and making the authentication process as unobtrusive as possible.
And though SMS has been around for quite a while, modern software and devices can make its use as an authentication factor surprisingly convenient — given some simple conditions are met. Mobile applications that call for OTPs can be set to recognise the incoming SMS messages with proper service names and metadata, automatically filling in the one-time passwords.
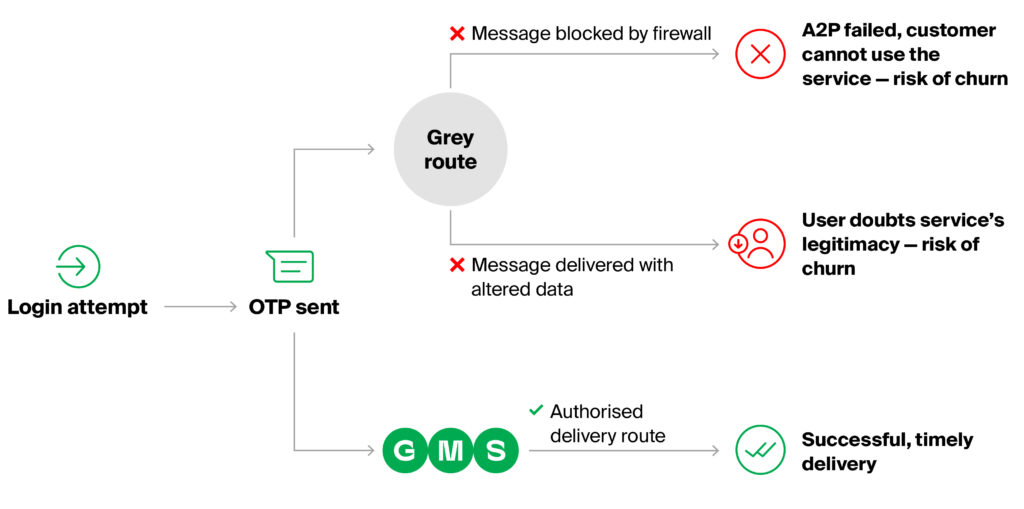
However, smooth authentication can only be achieved with the help of a reliable messaging partner like GMS, who will ensure that your OTP traffic is delivered unaltered and through legitimate channels. Otherwise, the password may not be recognised as such, and the user will have to type it in manually, undermining the effort to build a seamless and secure journey.
If you want to learn more about how you can protect your customers and enhance their experience, do not hesitate to reach out to us today!
Do not forget to download our cheat sheet to make sure your OTPs are always spot-on!

