Covid-19 has brought about a huge spike in SMS fraud as cybercriminals prey on people’s vulnerabilities during these challenging times. As mobile banking malware becomes more sophisticated, it is increasingly difficult for subscribers to differentiate fact from fiction, with many suffering financial losses as a result.
The general advice has been to avoid opening suspicious messages altogether. This erosion of trust and loss of potential SMS revenues spells bad news for mobile network operators.
The main culprits are SMS phishing or smishing attacks, which aim to obtain sensitive information like the subscriber’s personal and bank account data. Typically, a person is invited to click a link, call a phone number, or contact an email address provided by the attacker via SMS message and share their details.
A more recent and advanced menace is the FluBot, which combines smishing with trojan malware. It sets a new precedent with its spreading methods and DGA (Domain Generation Algorithms) implementations, as well as its software components. Let’s dissect the threats posed by this malware — and how MNOs can fight it.
FluBot malware — what is the fuss about?
FluBot is a new Android banking malware that uses overlay attacks to perform webview-based application phishing. The malware targets mobile banking and cryptocurrency applications primarily. However, it also gathers a wide range of user data from all applications installed on an infected device.
An attacker sends a fake SMS message “informing” the recipient about an undelivered parcel or a problem with a bank account. To make the message look more credible, culprits also frequently utilise SMS spoofing (falsifying the sender ID). This way, the fake messages appear in the same thread as previous messages from a legitimate sender.
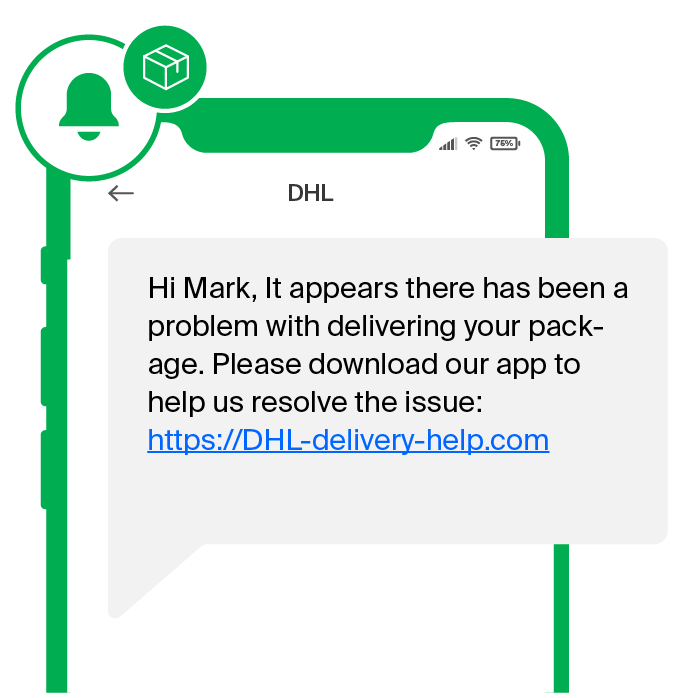
Following the links inside the fake message takes the subscribers to a legitimate website hacked by the criminals. Hacked web application servers are set up to contain the malware APK file. The user is instructed to allow external apps on their phone without explicitly stating that this requires changing the security settings. If the user goes on with it, a trojan malware is downloaded.
Once installed, FluBot malware instantly starts tracking applications launched on the device. Once a target application launch is detected, the malware begins an overlay attack by downloading the login page specially crafted for the opened target app. The downloaded webview phishing page is then laid over the target application almost instantaneously, so the user suspects nothing. Once the application credentials are entered into the overlayed phishing page, FluBot malware sends the credentials to the C&C (command and control) server controlled by the attacker.

Another danger of the FluBot malware is its ability to access a user’s contact book and send SMS text messages to subscribers in the directory in order to propagate itself. The FluBot owes its name to its spread rate and infection vector, that resemble the common flu.
According to FluBot — Malware Analysis Report by Prodaft, FluBot has spread to the UK, Germany, Hungary, Italy, Poland, and Spain. Having already collected 25% of Spanish mobile numbers, infected more than 60,000 victims and stolen over 11 million phone numbers, the malware shows no signs of slowing down.
According to experts, the threat actors are using different hacked web application servers in almost every message. This shows the FluBot operation’s level of sophistication, which distinguishes it from other consumer-grade banking malware.
The report also estimates that this malware is capable of collecting almost all phone numbers in Spain within 6 months if no action is taken. In other malware families, the SMS spreading functionality tends not to work as effectively. However, FluBot’s smishing module is well implemented and works in nearly all setups. In addition to the spreading method, its novel Domain Generation Algorithms approach makes it almost impossible to sinkhole the threat with traditional techniques. FluBot malware can also be easily adapted to be spread in different countries through a simple configuration change in its codebase.
The repercussions and possible solutions
The most immediate concern is the erosion of trust. When news of fraud or security breaches caused by SMS spreads, the public would inevitably question whether this channel is trustworthy. This can deal a massive blow to the operator’s revenues. If the subscribers start ignoring SMS, businesses would be forced to switch over to communication channels deemed secure by the audience — quite a grim perspective, considering A2P SMS revenues are estimated to reach $45.93 billion in 2021.
In a situation like this, releasing an official statement warning subscribers not to click on any suspicious links in SMS, would only make things worse for the operators, who essentially admit that their product is untrustworthy and insecure.
SMS firewalls are MNOs’ trusty tools for identifying and blocking spam and number spoofing. However, even the best SMS firewalls cannot automatically verify the security of a URL contained in the message. Since the hyperlink itself is the real threat, the firewall’s rules must be constantly updated and managed to have a chance against such types of fraud.
Therefore, the obvious solution would be blocking all messages that contain known malicious URLs. The problem is, such URLs are usually registered on the very same day of the attack and can be further altered down the line, which makes blacklisting these addresses ineffective, to say the least.
Turning the tables with Zero Trust SMS
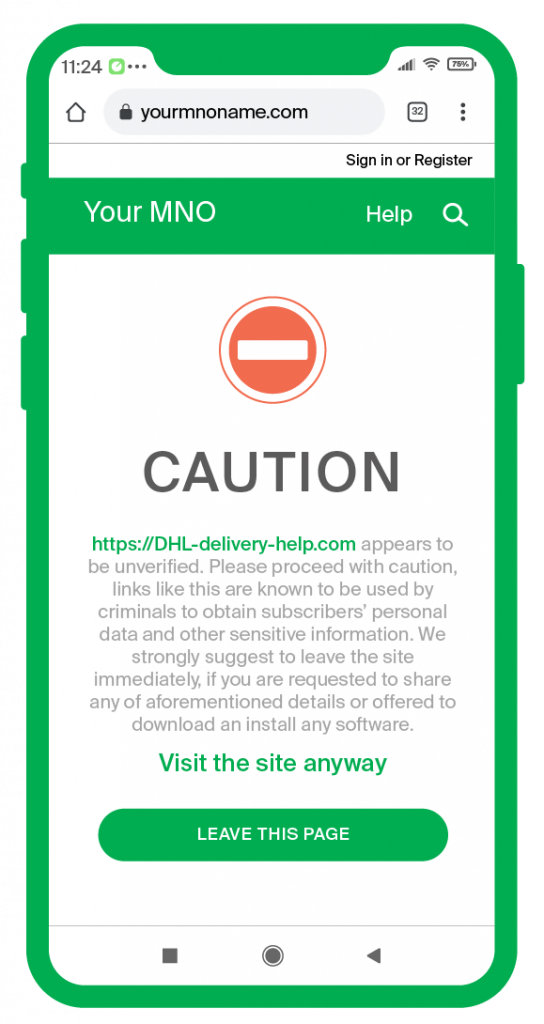
But what if you try a directly opposite approach, treating every URL delivered through SMS as dangerous unless authenticated as safe? The Zero Trust approach — a part of the GMS Messaging Protection offering — does just that.
This approach helps to stop smishing and malware from infiltrating your network and hurting your subscriber base, ensuring that every link sent to every subscriber is safe and secure. This is achieved by outrightly blocking the malicious links, while the yet not classified potentially dangerous links are delivered with a strong warning. As a result, you both protect and educate your subscribers, letting them know, which URLs are safe to open, and which have been blocked for their security.
Protecting your subscribers and revenues
Despite the obvious threat posed by the FluBot malware, GMS can provide MNOs with a unique opportunity to inform their subscribers about the credibility of every single link delivered to their handset, show their expertise, and cement their reputation as a caring and professional vendor, while securing revenues.
Contact our experts to learn more about GMS Messaging Protection today!

