As smartphones increasingly resemble personal computers, they begin to acquire the same kinds of vulnerabilities. Technical sophistication has made the humble mobile incredibly sophisticated but also gives opportunities to those with some programming skills and a desire to make a quick buck. With people using their phones for banking, receiving 2FA messages, or simply storing important data, they have become very tempting targets.
A worrying trend in recent years has been an increase in stories — usually on tech-oriented news sites such as Techspot or ZDNet — warning of a new virus or malware payload exploiting SMS texts to infect or spread between users. These aren’t just scare stories. The attacks themselves are on the rise, according to Kaspersky.
Perhaps as a consequence, we are increasingly seeing MNOs asking us if and how we can help them combat fraud and protect their subscribers against this particular threat. Fortunately, with the right tools and team, doing so can be comparatively straightforward. How to address SMS malware?
The threat
SMS malware has been a persistent problem for some time now, being listed among the 11 types of fraud identified by the MEF in 2016, and again in their 2019 mobile messaging fraud framework. There is good reason for concern. The fallout from an SMS virus or malware affects everyone in the messaging chain. Aggregators and MNOs suffer a loss of reputation, having seemingly casually passed on these messages without due diligence. The latter must also contend with the fact that fraudulent messages contribute to network congestion — even more so if the malware exploits the subscriber’s contact list.
And of course, subscribers suffer. The entire point of malware is to exploit someone’s device and use it to generate revenue. Fake messages add to their bill, and compromised data can be used for more damaging attacks elsewhere. If the experience is particularly bad, users may start wondering why their network didn’t do more to protect them from this threat.
The architecture of an SMS malware fraud
SMS malware typically consists of an SMS message containing a URL. The idea is to get the subscriber to open the link by making the message seem to come from a legitimate source, such as their bank.
Their aims and methods can be more variable. Some look like legitimate apps, which users download only to find their credentials compromised and bank details — or even their money — stolen. Others pose as links to content or websites, which secretly download ransomware in the background, forcing the user to pay to have their phone decrypted.
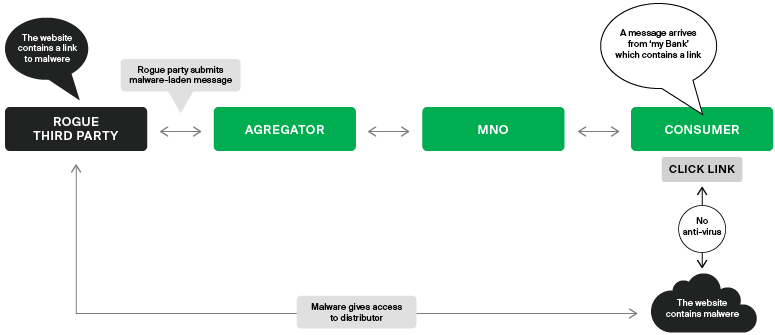
SMS malware also often plunders the victim’s contacts list, sending links to more people (hoping people will click on links from people they know and trust). In some cases, access to contacts is the primary purpose: 2017’s “ExpensiveWall” malware was installed under the guise of a regular app, and sent premium SMS messages to their contacts. In cases like this, the aim is not to “hack” the user’s data but to generate revenue from them through the SMSs the malware sends from their device.
Malware that sends messages — as either its primary or as a secondary objective — typically earns money by accruing premium charges via an aggregator. These aggregators usually lack sufficient experience of working with MNOs to spot problem messaging, and will trust that a messaging client is legitimate.
Combating SMS malware
Fortunately, addressing viruses and malware that exploit SMS can be done in much the same way as other messaging fraud. A rigorous SMS firewall implementation will detect messages containing suspect content. Some VAS implementations can even learn as they go, flagging up messages that look similar to previously identified scams and fraud.
An SMS firewall will check URLs in the same manner in which they check other content for blacklisted keywords, and thereby weed out messages containing suspicious links. It can then block or flag messages, preventing damage caused by malware-carrying SMS and alerting the MNO to fraud on their network. And naturally, if the malware is of the ExpensiveWall type, the firewall can detect fraudulent premium messages just like other types of spam.
The challenge here is that to do this effectively requires a good degree of vigilance and regular updates — since new scams, using new links, do not emerge according to a convenient schedule, and most use link-shortening domains, like bit.ly, to make it harder to see where a link actually leads.
This means that the MNO or their partners must be alert to new scams, and can’t merely rely on looking for URLs that appear similar to well-known sites. A trusted provider even has an advantage, in that they might cover many different networks in multiple countries, and when a threat arises in one, they can update the firewall rules for each of their clients so the threat cannot spread.
At GMS, we have the experience and global knowledge to weed out dangerous SMS messaging, leaving a clean, trustworthy channel, protecting subscribers and MNO alike. Contact our experts to find out more about the kinds of fraud against which we can protect you.

