With identity theft all the rage, digital identity authentication and validation measures are critical to ensuring Web and network infrastructure security in the public and private sectors. In this article, we take a closer look at digital identity and figure out the easiest ways to protect your customers and consumers’ digital IDs.
The benefits of digital ID
A digital identity or “digital ID” can be one or a couple of digital identifiers, like an email address, URL or domain name. Digital ID allows users to unlock value and benefit as they interact with enterprises, governments, and other individuals in many roles: as employees, consumers, entrepreneurs, taxpayers, and beneficiaries, etc. For instance, digital ID could help provide access to financial services for over 1.7 billion people currently financially excluded, according to the World Bank.
Protecting the digital ID
Just like other technological innovations such as social media or GPS, digital ID can create value or inflict harm. Without proper controls, digital IDs can be used by fraudsters against the interests of the ID owners.
With over 5.27 billion unique mobile phone users in the world today, it is only natural that mobile identity now lies at the heart of the digital economy. As an extension of digital identity provided via mobile networks or devices, it can both serve as an enabler for logging in and transacting — and to play a central role in protecting the digital identity.
To help to stop cybercriminals, you will require as many layers of protection as possible, and the multi-factor (MFA) and two-factor (2FA) authentication are just what you need.
Let’s begin with the two ways of employing MFA.
When to use…
Step-Up Authentication. This method helps prevent fraudsters from accessing user’s online accounts. It involves requesting users to authenticate themselves through the following factors during login:
- First, to provide something they know (password).
- Then to authenticate with a second factor via something they have (mobile phone, security key) or something they are (biometrics).
For example, the online banking platform requires the customer to provide a username and password, followed by the OTP, delivered to the user’s registered mobile number. In this case, the OTP serves as a second factor of authentication. Similarly, another 2FA factor can be used instead of sending OTP via SMS.
Adaptive Authentication. This method protects users from fraud when unusual account activity is detected. Based on previous user behaviour, they can be asked to authenticate themselves again if the actions performed do not match the previously recorded patterns. This authentication type uses something the user has or something they are as the authentication factor.
For example, a logged-in user to may be asked to authenticate themself in the following scenarios:
- The user orders an unusually high volume of products when they have never bought in bulk previously.
- When using a banking app, after multiple subsequent failed transaction requests.
The user-friendly ways to set up MFA
It is worth mentioning that the users themselves are usually the weakest elements of any protection. There are quite a few ways of introducing the MFA, and choosing the most user-friendly ones will help you ensure that your customers are using 2FA without being tempted to turn it off, rendering all your efforts futile. Let us take a look at the most user-friendly types of 2FA:
OTP (One-Time Passwords) — SMS or Voice
One-Time Passwords are the randomly generated sequences of either numbers or numbers and symbols, generated on the brand’s side and delivered to the user’s mobile number via SMS or voice call. The user then enters the OTP they received to finish the authentication.
Advantages:
- User-friendly
- Helps to protect a very broad audience
- Affordable
Disadvantages:
- Third parties can intercept SMS or voice calls
- A phone is required to complete authentication
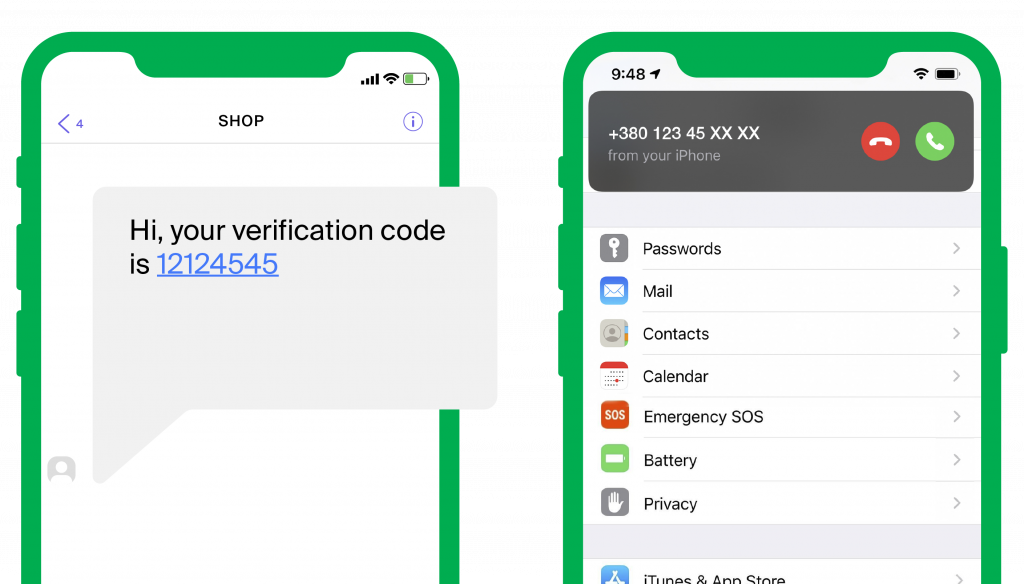
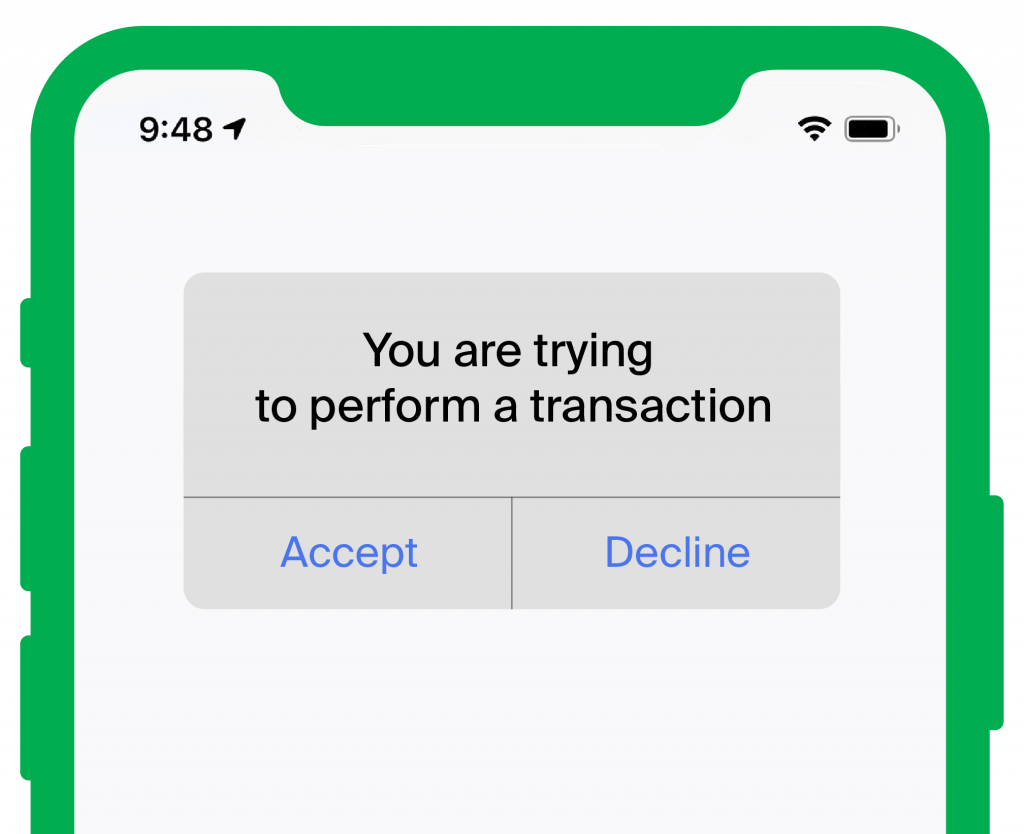
Push Notifications
Sending a push notification to a user, enables the person toeither accept or decline the access request with a single touch. This way, you can avoid using biometrics or entering an OTP for authentication, making it fairly convenient for the user. This is a highly secure 2FA method that helps fight phishing attacks. It is important to note that this method requires a smartphone, an application and an internet connection.
Advantages:
- Easy to use: a single click is necessary to allow or deny the target actions
- Secure: cannot be used until the mobile device is unlocked
Disadvantages:
- Requires a smartphone, an app and an internet connection
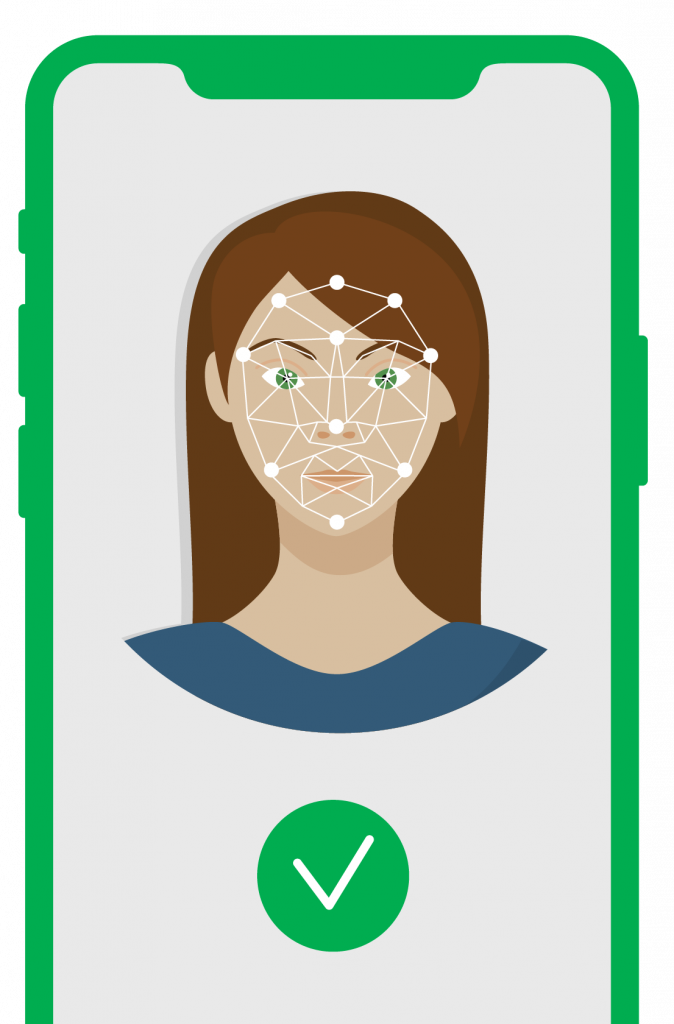
Biometric
Biometric authentication happens by using fingerprint, retina scan or facial recognition. It is used to ensure that only the user with corresponding biometric properties can access protected information or perform actions.
Advantages:
- Multiple options available: fingerprint, retina, face recognition
- User-friendly
Disadvantages:
- Requires additional hardware and software to read and verify biometric data
- The biometric data cannot be reset if compromised
Authenticator apps
The Authenticator apps use software-generated one-time passwords. To use this authentication method, also known as soft tokens, downloading and installing a 2FA app on the user’s mobile device is necessary.
Soft tokens are time-based, i.e. they expire after reaching the configured expiration time, making them more secure than static OTPs. This method requires a smartphone, but the internet connection is only necessary when setting up a user’s account.
Advantages:
- A single authenticator app can be utilised for multiple applications
- More secure when compared to static one-time passwords
- User-friendly
- Autonomous
Disadvantages:
- Requires additional software installation
- Requires a smartphone
In conclusion
While digital identity guides and offers plenty of benefits, making both individuals’ and enterprises’ daily operations more manageable and seamless, security is still a concern. Contact our experts now to learn how GMS can help to protect your customer and employee data with MFA.

